Protecting your hosted e-mail from spoofing
For a couple of months I’ve been getting a trickle of badly-put-together (but frustratingly well-spoofed) extortion spam at my main website e-mail address.
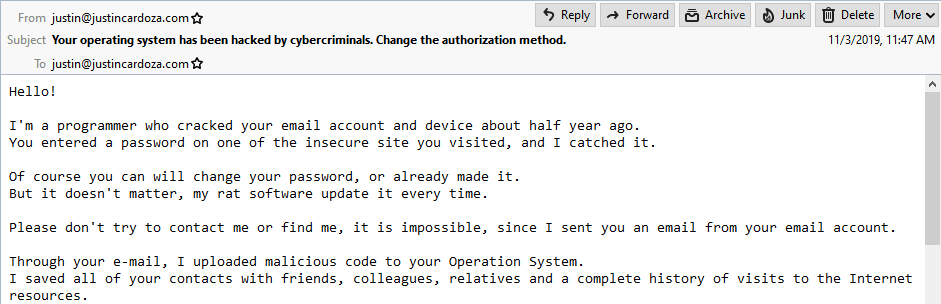
Some of the gems not shown here are “I am in shock of your reach fantasies!” and “My Trojan have auto alert, after this email is looked, I will be know it!”… then they ask for $928 in Bitcoin.
It didn’t bother me that much beyond my inability to track down the culprits (the spammers seem to be mainly using other people’s vulnerable ADSL routers in various countries to send their spam), but what really crossed the line for me was when I started getting delivery failure notifications for spam messages to other people:
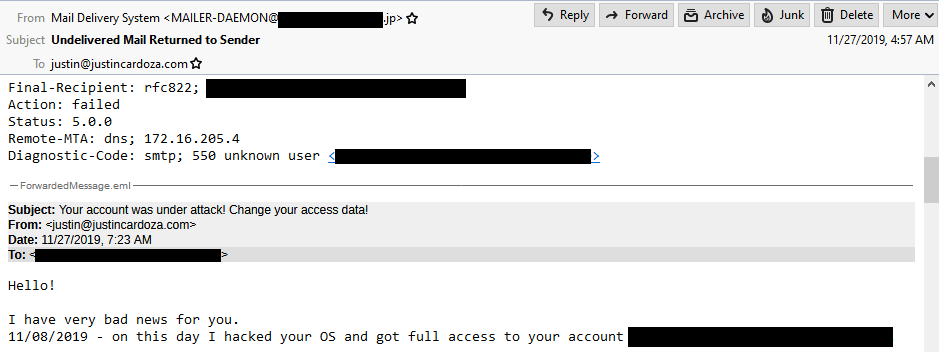
Same basic idea, but this time they’re sending it to other people and putting my address on it. Destination address censored in case it does actually belong to someone.
Yes, the spammers were spoofing their messages to come from my address, and my domain wasn’t configured to give mail servers any rules about who is allowed to send e-mail from my address by default, so everything was being allowed through. I found some great resources like this Lifehacker article that explain how e-mail spoofing works, and I determined that I needed to add a Sender Policy Framework (SPF) record and a “Domain-based Message Authentication, Reporting & Conformance” (DMARC) record to my DNS settings.
Long story short, SPF tells mail servers who is allowed to send e-mail from a given domain name and DMARC tells mail servers what to do if a message is sent from an unauthorized server. They work together with SPF forming a security foundation for DMARC to build on. They’re both specified as TXT records and each has a specific format. I found some extremely helpful resources from DMARC Analyzer for putting together those records: they have guides for SPF and DMARC and even an online record checker for verifying that everything looks good.
I set up my DNS records so hopefully mail servers will now reject messages that I don’t personally send through my server, and I should now get reports about any future spoofing activity. I plan to write a follow-up post if I get any interesting results back from that. For now, stay safe out there and don’t give any Bitcoin to strangers!
